I was writing another blog post and I realized that I keep repeating how to do the same things, so I decided to write some tutorial-ish things and just link them.
Burp uses custom certificates to Man-in-the-Middle (MitM) the traffic. All of these certificates are signed by Burp's root Certificate Authority (CA). Each installation of Burp generates its own root CA that needs to be installed in the browser or Operating System's certificate store to be recognized properly. Otherwise browsers will return warnings and some thick client applications will not recognize these certificates as valid.
Each installation of Burp generates its own root CA so it is unlikely that others can gain access to it and sign certificates to MitM your connection. To get the certificate's private key, the attackers need to get to your local machine and if so they have better ways to look at your traffic anyway.
Alternate instructions by Portswigger: https://support.portswigger.net/customer/en/portal/articles/1783075-installing-burp-s-ca-certificate-in-your-browser
For instructions on installing/removing Burp's CA in other browsers and devices please use Portswigger's website: https://support.portswigger.net/customer/en/portal/articles/1783075-installing-burp-s-ca-certificate-in-your-browser.
Note: These instructions are for Burp version 1.6.37 Pro and 1.6.32 Free. As long as I remember (v1.5) these instructions have not changed, although they may change in the future but I really doubt it.
Obtaining Burp's Root CA
This tutorial assumes you have already installed Burp (both free and pro version have the same) and you are running Windows. Although accessing the certificate is OS agnostic.
Using a Browser
Open up your browser and navigate to the following URL http://burp/ or http://127.0.0.1:8080 (default settings for Burp's proxy listener), If you have set-up Burp's proxy listener on a different port, use that instead of 8080. Please not that if you have disabled the Burp's web interface in Proxy > Options > Miscellaneous > Disable web interface at http://burp, this method will not work. You either have to enable the web interface or use the other method.
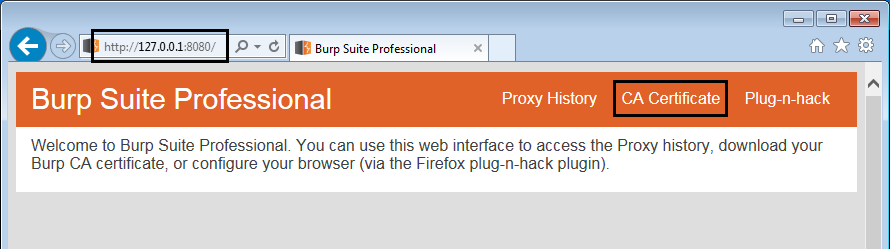 Burp's web interface
Burp's web interfaceClick on CA Certificate to begin downloading the certificate.
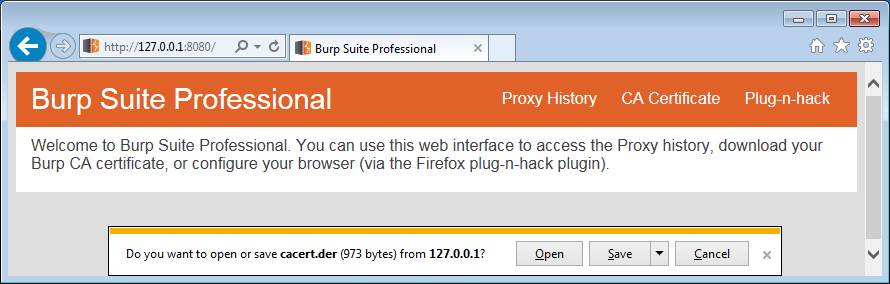 Downloading Burp's CA
Downloading Burp's CAUsing Burp's Certificate Export Functionality
If you have disabled Burp's web interface, you can use Burp to export the certificate directly. This functionality also allows you to export the certificate along with its private key to use in other applications. This is useful if you want to sign your own custom certificates but do not want to generate a new root CA like I did for Hipchat.
Open Burp and navigate to Proxy > Options. Look under Proxy Listeners at the top of the page for a button named Import / export CA certificate. Notice that you can also re-generate the certificate.
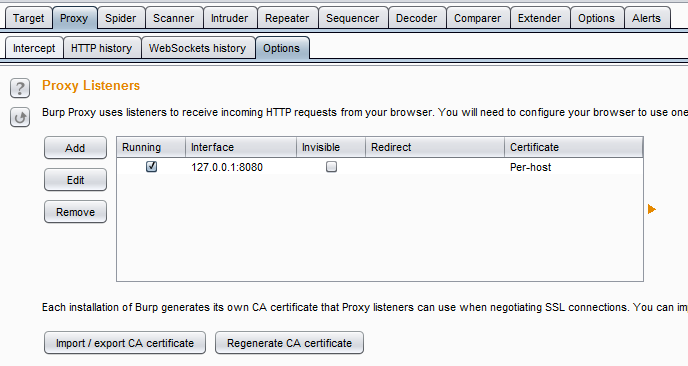 Burp's import/export funcationality
Burp's import/export funcationalityClick the button and you can use the wizard to export Burp's root CA. At this stage we only need the certificate (and not the private key). Select the top option under Export which is Certificate in DER format.
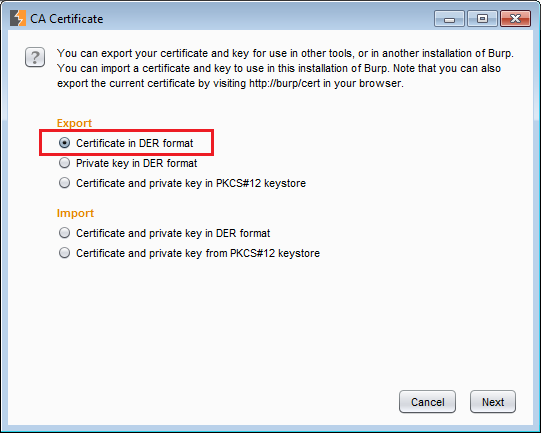 Exporting the certificate in Burp
Exporting the certificate in BurpClick next and then click on Select file.
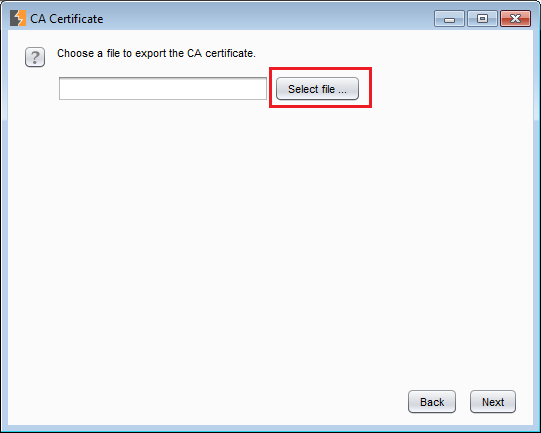 Select file
Select fileNow select a filename and path for the certificate.
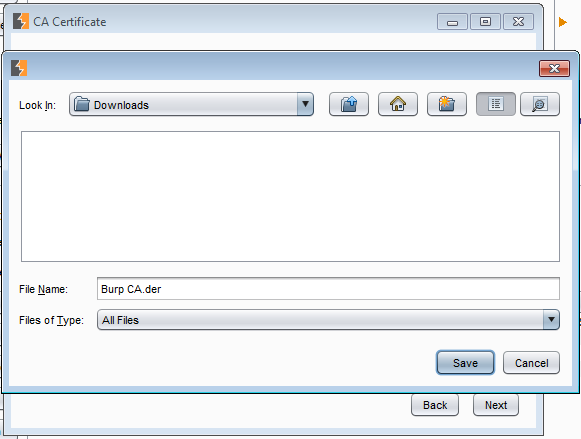 Select path and filename
Select path and filenameClick Next and then finally Close.
Installing Burp's Root CA in Windows Certificate Store
Double click the certificate and then c lick Install Certificate.
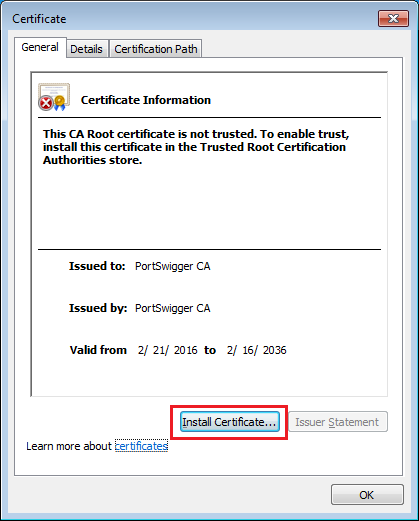 Install certificate button
Install certificate buttonClick Next only once until you reach the following screen where you can choose the certificate store to save the certificate. Select Place all certificates in the following store and then select Browse.
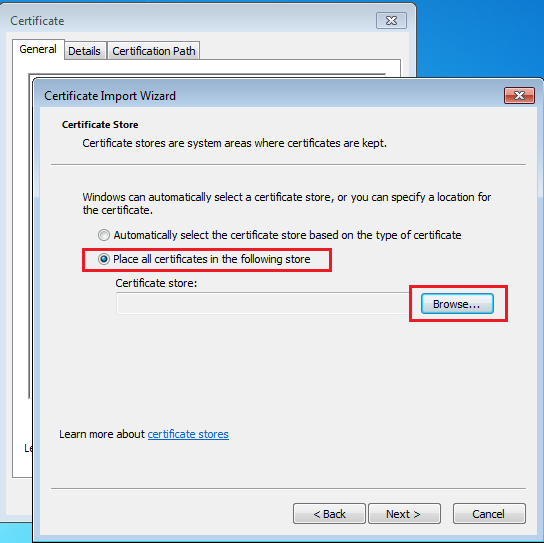 Selecting the certificate store
Selecting the certificate storeSelect Trusted Root Certification Authorities. And press Ok and then Next.
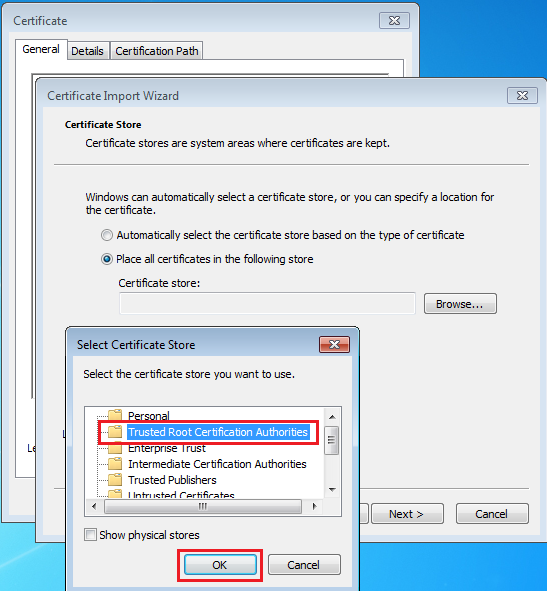 Selecting the root CA certificate store
Selecting the root CA certificate storeIf you did not have Burp's CA installed, you will get a security warning screen after clicking Finish.
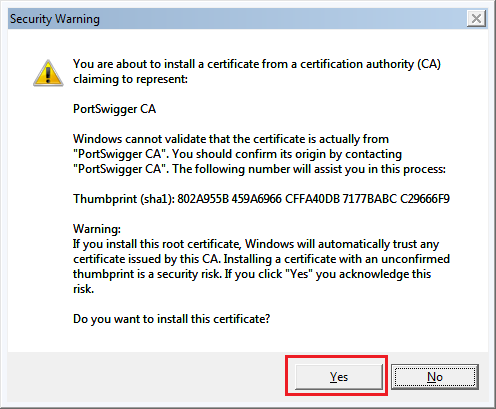 Security warning when installing a root CA
Security warning when installing a root CAPress Yes and you should get a Import was successful message.
Now any certificate signed by Burp will be valid in most thick client applications, Internet Explorer and Chrome. Note that Firefox has its own certificate store and proxy settings.